'I Hope You Publish This': NSA Broke Into Google, Yahoo Data Centers
'The NSA does not keep everything it collects, but it keeps a lot,' reports the Washington Post
In a report that terms the specific NSA surveillance program as "unusually aggressive," the newspaper claims that leaked documents provided by whistleblower Edward Snowden show how the operation, codenamed MUSCULAR, allowed the agency to access the "cloud networks" of the two internet giants and "collect at will from among hundreds of millions of user accounts, many of them belonging to Americans."
Two engineers with close ties to Google exploded in profanity when they saw the leaked drawing from the NSA: "I hope you publish this," one of them said.
"The NSA does not keep everything it collects," the Post reports, "but it keeps a lot."
Though the stream of information generated by the Snowden leaks seems endless, these latest revelations come amid growing concern both in the U.S. and abroad about the unrivaled power of the NSA when it comes to accessing information that was otherwise thought protected.
In this case, it is the internet giants themselves who seem most caught off guard over the revelations. Since the Snowden leaks first began, these companies (along with others) have been criticized for allowing the NSA specific kinds of access to their customer data. As the Post reports, however, disclosure of the MUSCULAR program becomes "especially striking,"
because the NSA, under a separate program known as PRISM, has front-door access to Google and Yahoo user accounts through a court-approved process.
The MUSCULAR project appears to be an unusually aggressive use of NSA tradecraft against flagship American companies. The agency is built for high-tech spying, with a wide range of digital tools, but it has not been known to use them routinely against U.S. companies.
When asked by the Post if they were aware of the program, both Yahoo! and Google adamantly said they did not know and expressed deep concern--anger, in fact--that the NSA had possibly infiltrated their private, highly secure, "cloud" networks.
As the Post explains:
In order for the data centers to operate effectively, they synchronize high volumes of information about account holders. Yahoo's internal network, for example, sometimes transmits entire e-mail archives -- years of messages and attachments -- from one data center to another.
Tapping the Google and Yahoo clouds allows the NSA to intercept communications in real time and to take "a retrospective look at target activity," according to one internal NSA document.
In order to obtain free access to data center traffic, the NSA had to circumvent gold standard security measures. Google "goes to great lengths to protect the data and intellectual property in these centers," according to one of the company's blog posts, with tightly audited access controls, heat sensitive cameras, round-the-clock guards and biometric verification of identities.
Google and Yahoo also pay for premium data links, designed to be faster, more reliable and more secure. In recent years, each of them is said to have bought or leased thousands of miles of fiber optic cables for their own exclusive use. They had reason to think, insiders said, that their private, internal networks were safe from prying eyes.
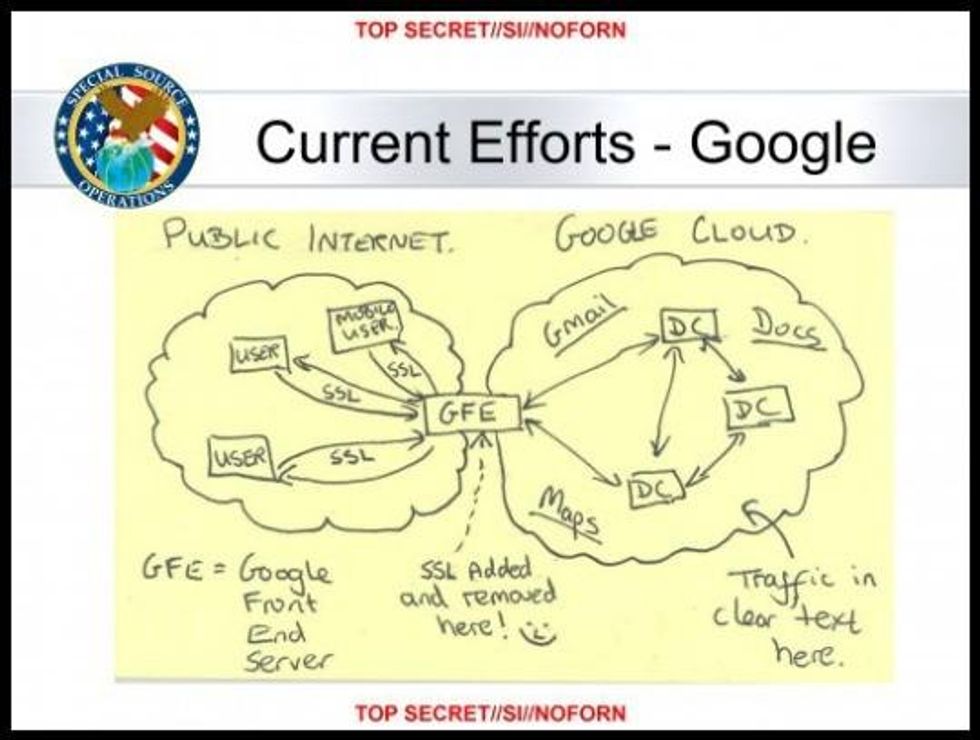
In an NSA presentation slide on "Google Cloud Exploitation," however, a sketch shows where the "Public Internet" meets the internal "Google Cloud" where their data resides. In hand-printed letters, the drawing notes that encryption is "added and removed here!" The artist adds a smiley face, a cheeky celebration of victory over Google security.
Two engineers with close ties to Google exploded in profanity when they saw the drawing. "I hope you publish this," one of them said.
Whether those in the outraged public will find sympathy with the likes of Google and Yahoo!, the exposure of MUSCULAR shows the degree to which online data--even that which was thought to be more secure--is susceptible to the reach of the NSA.
One of the other key takeaways from the Post reporting is how this particular program seemed to target communication hubs and data centers located outside of the U.S., showing that legal requirements, though clearly not effective overall, certainly have an impact on the manner in which the NSA operates. Again, from the report:
Intercepting communications overseas has clear advantages for the NSA, with looser restrictions and less oversight. NSA documents about the effort refer directly to "full take," "bulk access" and "high volume" operations on Yahoo and Google networks. Such large-scale collection of Internet content would be illegal in the United States, but the operations take place overseas, where the NSA is allowed to presume that anyone using a foreign data link is a foreigner.
Outside U.S. territory, statutory restrictions on surveillance seldom apply and the Foreign Intelligence Surveillance Court has no jurisdiction. Senate Intelligence Committee Chairwoman Dianne Feinstein has acknowledged that Congress conducts little oversight of intelligence-gathering under the presidential authority of Executive Order 12333 , which defines the basic powers and responsibilities of the intelligence agencies.
John Schindler, a former NSA chief analyst and frequent defender who teaches at the Naval War College, said it was obvious why the agency would prefer to avoid restrictions where it can.
"Look, NSA has platoons of lawyers and their entire job is figuring out how to stay within the law and maximize collection by exploiting every loophole," he said. "It's fair to say the rules are less restrictive under Executive Order 12333 than they are under FISA."
___________________________________________
An Urgent Message From Our Co-Founder
Dear Common Dreams reader, The U.S. is on a fast track to authoritarianism like nothing I've ever seen. Meanwhile, corporate news outlets are utterly capitulating to Trump, twisting their coverage to avoid drawing his ire while lining up to stuff cash in his pockets. That's why I believe that Common Dreams is doing the best and most consequential reporting that we've ever done. Our small but mighty team is a progressive reporting powerhouse, covering the news every day that the corporate media never will. Our mission has always been simple: To inform. To inspire. And to ignite change for the common good. Now here's the key piece that I want all our readers to understand: None of this would be possible without your financial support. That's not just some fundraising cliche. It's the absolute and literal truth. We don't accept corporate advertising and never will. We don't have a paywall because we don't think people should be blocked from critical news based on their ability to pay. Everything we do is funded by the donations of readers like you. Will you donate now to help power the nonprofit, independent reporting of Common Dreams? Thank you for being a vital member of our community. Together, we can keep independent journalism alive when it’s needed most. - Craig Brown, Co-founder |

In a report that terms the specific NSA surveillance program as "unusually aggressive," the newspaper claims that leaked documents provided by whistleblower Edward Snowden show how the operation, codenamed MUSCULAR, allowed the agency to access the "cloud networks" of the two internet giants and "collect at will from among hundreds of millions of user accounts, many of them belonging to Americans."
Two engineers with close ties to Google exploded in profanity when they saw the leaked drawing from the NSA: "I hope you publish this," one of them said.
"The NSA does not keep everything it collects," the Post reports, "but it keeps a lot."
Though the stream of information generated by the Snowden leaks seems endless, these latest revelations come amid growing concern both in the U.S. and abroad about the unrivaled power of the NSA when it comes to accessing information that was otherwise thought protected.
In this case, it is the internet giants themselves who seem most caught off guard over the revelations. Since the Snowden leaks first began, these companies (along with others) have been criticized for allowing the NSA specific kinds of access to their customer data. As the Post reports, however, disclosure of the MUSCULAR program becomes "especially striking,"
because the NSA, under a separate program known as PRISM, has front-door access to Google and Yahoo user accounts through a court-approved process.
The MUSCULAR project appears to be an unusually aggressive use of NSA tradecraft against flagship American companies. The agency is built for high-tech spying, with a wide range of digital tools, but it has not been known to use them routinely against U.S. companies.
When asked by the Post if they were aware of the program, both Yahoo! and Google adamantly said they did not know and expressed deep concern--anger, in fact--that the NSA had possibly infiltrated their private, highly secure, "cloud" networks.
As the Post explains:
In order for the data centers to operate effectively, they synchronize high volumes of information about account holders. Yahoo's internal network, for example, sometimes transmits entire e-mail archives -- years of messages and attachments -- from one data center to another.
Tapping the Google and Yahoo clouds allows the NSA to intercept communications in real time and to take "a retrospective look at target activity," according to one internal NSA document.
In order to obtain free access to data center traffic, the NSA had to circumvent gold standard security measures. Google "goes to great lengths to protect the data and intellectual property in these centers," according to one of the company's blog posts, with tightly audited access controls, heat sensitive cameras, round-the-clock guards and biometric verification of identities.
Google and Yahoo also pay for premium data links, designed to be faster, more reliable and more secure. In recent years, each of them is said to have bought or leased thousands of miles of fiber optic cables for their own exclusive use. They had reason to think, insiders said, that their private, internal networks were safe from prying eyes.
In an NSA presentation slide on "Google Cloud Exploitation," however, a sketch shows where the "Public Internet" meets the internal "Google Cloud" where their data resides. In hand-printed letters, the drawing notes that encryption is "added and removed here!" The artist adds a smiley face, a cheeky celebration of victory over Google security.
Two engineers with close ties to Google exploded in profanity when they saw the drawing. "I hope you publish this," one of them said.
Whether those in the outraged public will find sympathy with the likes of Google and Yahoo!, the exposure of MUSCULAR shows the degree to which online data--even that which was thought to be more secure--is susceptible to the reach of the NSA.
One of the other key takeaways from the Post reporting is how this particular program seemed to target communication hubs and data centers located outside of the U.S., showing that legal requirements, though clearly not effective overall, certainly have an impact on the manner in which the NSA operates. Again, from the report:
Intercepting communications overseas has clear advantages for the NSA, with looser restrictions and less oversight. NSA documents about the effort refer directly to "full take," "bulk access" and "high volume" operations on Yahoo and Google networks. Such large-scale collection of Internet content would be illegal in the United States, but the operations take place overseas, where the NSA is allowed to presume that anyone using a foreign data link is a foreigner.
Outside U.S. territory, statutory restrictions on surveillance seldom apply and the Foreign Intelligence Surveillance Court has no jurisdiction. Senate Intelligence Committee Chairwoman Dianne Feinstein has acknowledged that Congress conducts little oversight of intelligence-gathering under the presidential authority of Executive Order 12333 , which defines the basic powers and responsibilities of the intelligence agencies.
John Schindler, a former NSA chief analyst and frequent defender who teaches at the Naval War College, said it was obvious why the agency would prefer to avoid restrictions where it can.
"Look, NSA has platoons of lawyers and their entire job is figuring out how to stay within the law and maximize collection by exploiting every loophole," he said. "It's fair to say the rules are less restrictive under Executive Order 12333 than they are under FISA."
___________________________________________

In a report that terms the specific NSA surveillance program as "unusually aggressive," the newspaper claims that leaked documents provided by whistleblower Edward Snowden show how the operation, codenamed MUSCULAR, allowed the agency to access the "cloud networks" of the two internet giants and "collect at will from among hundreds of millions of user accounts, many of them belonging to Americans."
Two engineers with close ties to Google exploded in profanity when they saw the leaked drawing from the NSA: "I hope you publish this," one of them said.
"The NSA does not keep everything it collects," the Post reports, "but it keeps a lot."
Though the stream of information generated by the Snowden leaks seems endless, these latest revelations come amid growing concern both in the U.S. and abroad about the unrivaled power of the NSA when it comes to accessing information that was otherwise thought protected.
In this case, it is the internet giants themselves who seem most caught off guard over the revelations. Since the Snowden leaks first began, these companies (along with others) have been criticized for allowing the NSA specific kinds of access to their customer data. As the Post reports, however, disclosure of the MUSCULAR program becomes "especially striking,"
because the NSA, under a separate program known as PRISM, has front-door access to Google and Yahoo user accounts through a court-approved process.
The MUSCULAR project appears to be an unusually aggressive use of NSA tradecraft against flagship American companies. The agency is built for high-tech spying, with a wide range of digital tools, but it has not been known to use them routinely against U.S. companies.
When asked by the Post if they were aware of the program, both Yahoo! and Google adamantly said they did not know and expressed deep concern--anger, in fact--that the NSA had possibly infiltrated their private, highly secure, "cloud" networks.
As the Post explains:
In order for the data centers to operate effectively, they synchronize high volumes of information about account holders. Yahoo's internal network, for example, sometimes transmits entire e-mail archives -- years of messages and attachments -- from one data center to another.
Tapping the Google and Yahoo clouds allows the NSA to intercept communications in real time and to take "a retrospective look at target activity," according to one internal NSA document.
In order to obtain free access to data center traffic, the NSA had to circumvent gold standard security measures. Google "goes to great lengths to protect the data and intellectual property in these centers," according to one of the company's blog posts, with tightly audited access controls, heat sensitive cameras, round-the-clock guards and biometric verification of identities.
Google and Yahoo also pay for premium data links, designed to be faster, more reliable and more secure. In recent years, each of them is said to have bought or leased thousands of miles of fiber optic cables for their own exclusive use. They had reason to think, insiders said, that their private, internal networks were safe from prying eyes.
In an NSA presentation slide on "Google Cloud Exploitation," however, a sketch shows where the "Public Internet" meets the internal "Google Cloud" where their data resides. In hand-printed letters, the drawing notes that encryption is "added and removed here!" The artist adds a smiley face, a cheeky celebration of victory over Google security.
Two engineers with close ties to Google exploded in profanity when they saw the drawing. "I hope you publish this," one of them said.
Whether those in the outraged public will find sympathy with the likes of Google and Yahoo!, the exposure of MUSCULAR shows the degree to which online data--even that which was thought to be more secure--is susceptible to the reach of the NSA.
One of the other key takeaways from the Post reporting is how this particular program seemed to target communication hubs and data centers located outside of the U.S., showing that legal requirements, though clearly not effective overall, certainly have an impact on the manner in which the NSA operates. Again, from the report:
Intercepting communications overseas has clear advantages for the NSA, with looser restrictions and less oversight. NSA documents about the effort refer directly to "full take," "bulk access" and "high volume" operations on Yahoo and Google networks. Such large-scale collection of Internet content would be illegal in the United States, but the operations take place overseas, where the NSA is allowed to presume that anyone using a foreign data link is a foreigner.
Outside U.S. territory, statutory restrictions on surveillance seldom apply and the Foreign Intelligence Surveillance Court has no jurisdiction. Senate Intelligence Committee Chairwoman Dianne Feinstein has acknowledged that Congress conducts little oversight of intelligence-gathering under the presidential authority of Executive Order 12333 , which defines the basic powers and responsibilities of the intelligence agencies.
John Schindler, a former NSA chief analyst and frequent defender who teaches at the Naval War College, said it was obvious why the agency would prefer to avoid restrictions where it can.
"Look, NSA has platoons of lawyers and their entire job is figuring out how to stay within the law and maximize collection by exploiting every loophole," he said. "It's fair to say the rules are less restrictive under Executive Order 12333 than they are under FISA."
___________________________________________

