

SUBSCRIBE TO OUR FREE NEWSLETTER
Daily news & progressive opinion—funded by the people, not the corporations—delivered straight to your inbox.
5
#000000
#FFFFFF
To donate by check, phone, or other method, see our More Ways to Give page.


Daily news & progressive opinion—funded by the people, not the corporations—delivered straight to your inbox.
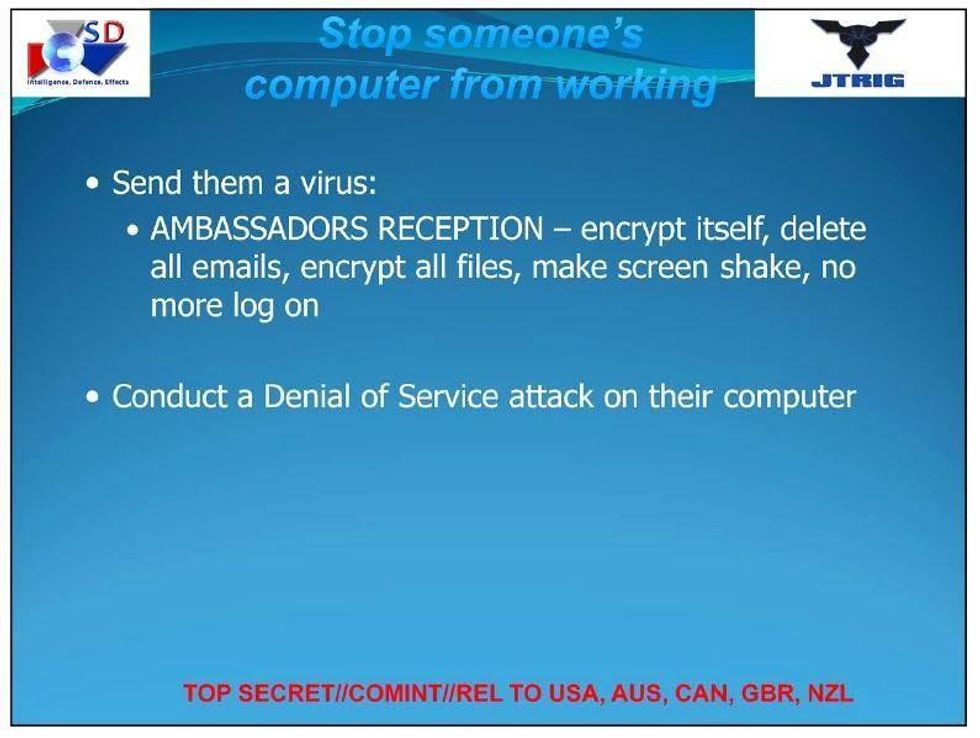
Focused on a secret branch within the GCHQ called the Joint Threat Research and Intelligence Group (JTRIG), the documents obtained by NBC News show that the operations of the group included "releasing computer viruses, spying on journalists and diplomats, jamming phones and computers, and using sex to lure targets into 'honey traps'" in order to "go on offense and attack adversaries."
The new reporting follows on one NBC published earlier this week highlighting other Snowden documents that revealed the existence of the JTRIG for the very first time. Journalist Glenn Greenwald is listed as 'special contributor' for both stories.
As the latest story hit the wire, Greenwald sent out a series of tweets remarking on the significance of the latest revelations and pointing to specific documents explored in the report:
As NBC reports:
According to the documents, which come from presentations prepped in 2010 and 2012 for NSA cyber spy conferences, the agency's goal was to "destroy, deny, degrade [and] disrupt" enemies by "discrediting" them, planting misinformation and shutting down their communications.
Both PowerPoint presentations describe "Effects" campaigns that are broadly divided into two categories: cyber attacks and propaganda operations. The propaganda camp aigns use deception, mass messaging and "pushing stories" via Twitter, Flickr, Facebook and YouTube. JTRIG also uses "false flag" operations, in which British agents carry out online actions that are designed to look like they were performed by one of Britain's adversaries.
Targeting Journalists
In one striking revelation contained in the documents, the JTRIG seems have developed a plan to embroil journalists in their intelligence operations.
The 2010 presentation also describes another potential operation that would utilize a technique called "credential harvesting" to select journalists who could be used to spread information. According to intelligence sources, spies considered using electronic snooping to identify non-British journalists who would then be manipulated to feed information to the target of a covert campaign. Apparently, the journalist's job would provide access to the targeted individual, perhaps for an interview. The documents do not specify whether the journalists would be aware or unaware that they were being used to funnel information.
The executive director of the Committee to Protect Journalists, Joel Simon, said that the revelation about "credential harvesting" should serve as a "wake up call" to journalists that intelligence agencies can monitor their communications. Simon also said that governments put all journalists at risk when they use even one for an intelligence operation.
"All journalists generally are then vulnerable to the charge that they work at the behest of an intelligence agency," said Simon.
The journalist operation was never put into action, according to sources, but other techniques described in the documents [...] have definitely been used to attack adversaries.
_____________________________________
Dear Common Dreams reader, The U.S. is on a fast track to authoritarianism like nothing I've ever seen. Meanwhile, corporate news outlets are utterly capitulating to Trump, twisting their coverage to avoid drawing his ire while lining up to stuff cash in his pockets. That's why I believe that Common Dreams is doing the best and most consequential reporting that we've ever done. Our small but mighty team is a progressive reporting powerhouse, covering the news every day that the corporate media never will. Our mission has always been simple: To inform. To inspire. And to ignite change for the common good. Now here's the key piece that I want all our readers to understand: None of this would be possible without your financial support. That's not just some fundraising cliche. It's the absolute and literal truth. We don't accept corporate advertising and never will. We don't have a paywall because we don't think people should be blocked from critical news based on their ability to pay. Everything we do is funded by the donations of readers like you. Will you donate now to help power the nonprofit, independent reporting of Common Dreams? Thank you for being a vital member of our community. Together, we can keep independent journalism alive when it’s needed most. - Craig Brown, Co-founder |

Focused on a secret branch within the GCHQ called the Joint Threat Research and Intelligence Group (JTRIG), the documents obtained by NBC News show that the operations of the group included "releasing computer viruses, spying on journalists and diplomats, jamming phones and computers, and using sex to lure targets into 'honey traps'" in order to "go on offense and attack adversaries."
The new reporting follows on one NBC published earlier this week highlighting other Snowden documents that revealed the existence of the JTRIG for the very first time. Journalist Glenn Greenwald is listed as 'special contributor' for both stories.
As the latest story hit the wire, Greenwald sent out a series of tweets remarking on the significance of the latest revelations and pointing to specific documents explored in the report:
As NBC reports:
According to the documents, which come from presentations prepped in 2010 and 2012 for NSA cyber spy conferences, the agency's goal was to "destroy, deny, degrade [and] disrupt" enemies by "discrediting" them, planting misinformation and shutting down their communications.
Both PowerPoint presentations describe "Effects" campaigns that are broadly divided into two categories: cyber attacks and propaganda operations. The propaganda camp aigns use deception, mass messaging and "pushing stories" via Twitter, Flickr, Facebook and YouTube. JTRIG also uses "false flag" operations, in which British agents carry out online actions that are designed to look like they were performed by one of Britain's adversaries.
Targeting Journalists
In one striking revelation contained in the documents, the JTRIG seems have developed a plan to embroil journalists in their intelligence operations.
The 2010 presentation also describes another potential operation that would utilize a technique called "credential harvesting" to select journalists who could be used to spread information. According to intelligence sources, spies considered using electronic snooping to identify non-British journalists who would then be manipulated to feed information to the target of a covert campaign. Apparently, the journalist's job would provide access to the targeted individual, perhaps for an interview. The documents do not specify whether the journalists would be aware or unaware that they were being used to funnel information.
The executive director of the Committee to Protect Journalists, Joel Simon, said that the revelation about "credential harvesting" should serve as a "wake up call" to journalists that intelligence agencies can monitor their communications. Simon also said that governments put all journalists at risk when they use even one for an intelligence operation.
"All journalists generally are then vulnerable to the charge that they work at the behest of an intelligence agency," said Simon.
The journalist operation was never put into action, according to sources, but other techniques described in the documents [...] have definitely been used to attack adversaries.
_____________________________________

Focused on a secret branch within the GCHQ called the Joint Threat Research and Intelligence Group (JTRIG), the documents obtained by NBC News show that the operations of the group included "releasing computer viruses, spying on journalists and diplomats, jamming phones and computers, and using sex to lure targets into 'honey traps'" in order to "go on offense and attack adversaries."
The new reporting follows on one NBC published earlier this week highlighting other Snowden documents that revealed the existence of the JTRIG for the very first time. Journalist Glenn Greenwald is listed as 'special contributor' for both stories.
As the latest story hit the wire, Greenwald sent out a series of tweets remarking on the significance of the latest revelations and pointing to specific documents explored in the report:
As NBC reports:
According to the documents, which come from presentations prepped in 2010 and 2012 for NSA cyber spy conferences, the agency's goal was to "destroy, deny, degrade [and] disrupt" enemies by "discrediting" them, planting misinformation and shutting down their communications.
Both PowerPoint presentations describe "Effects" campaigns that are broadly divided into two categories: cyber attacks and propaganda operations. The propaganda camp aigns use deception, mass messaging and "pushing stories" via Twitter, Flickr, Facebook and YouTube. JTRIG also uses "false flag" operations, in which British agents carry out online actions that are designed to look like they were performed by one of Britain's adversaries.
Targeting Journalists
In one striking revelation contained in the documents, the JTRIG seems have developed a plan to embroil journalists in their intelligence operations.
The 2010 presentation also describes another potential operation that would utilize a technique called "credential harvesting" to select journalists who could be used to spread information. According to intelligence sources, spies considered using electronic snooping to identify non-British journalists who would then be manipulated to feed information to the target of a covert campaign. Apparently, the journalist's job would provide access to the targeted individual, perhaps for an interview. The documents do not specify whether the journalists would be aware or unaware that they were being used to funnel information.
The executive director of the Committee to Protect Journalists, Joel Simon, said that the revelation about "credential harvesting" should serve as a "wake up call" to journalists that intelligence agencies can monitor their communications. Simon also said that governments put all journalists at risk when they use even one for an intelligence operation.
"All journalists generally are then vulnerable to the charge that they work at the behest of an intelligence agency," said Simon.
The journalist operation was never put into action, according to sources, but other techniques described in the documents [...] have definitely been used to attack adversaries.
_____________________________________